Recently, the National Computer Virus Emergency Response Center and the National Engineering Laboratory of Computer Virus Prevention and Control Technology relied on the national Computer Virus Collaborative analysis PlatformThe Android platform mobile phone trojan virus that imitated DeepSeek's official App was captured and found in our country.。
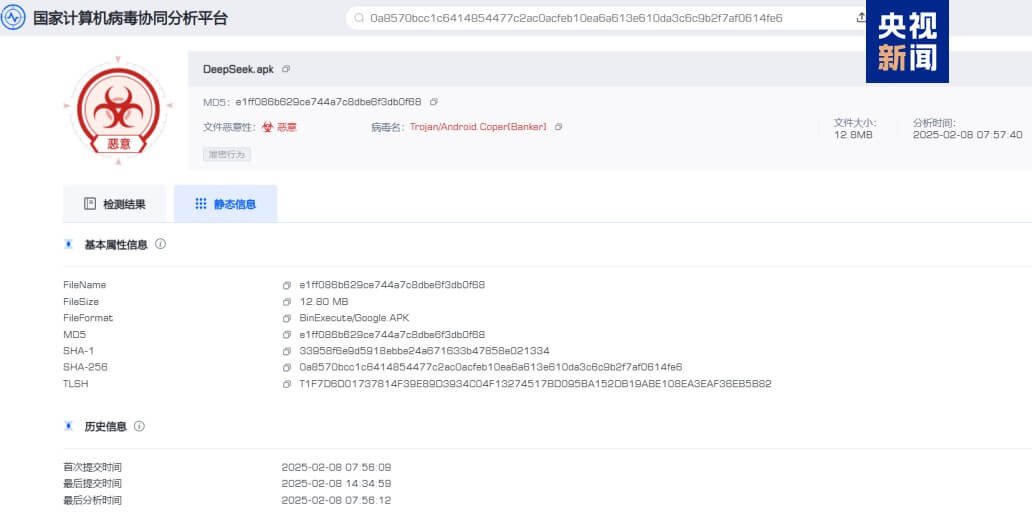
Related virus sample information
Once the user clicks to run the counterfeit app, the app will prompt the user“Application update required”, and induce the user to click the "Update” button. After the user clicks,It will prompt the installation of the so-called ”new version" of the DeepSeek application, which is actually a sub-installation package containing malicious code, and will induce the user to grant it permission to run and use barrier-free services in the background.。
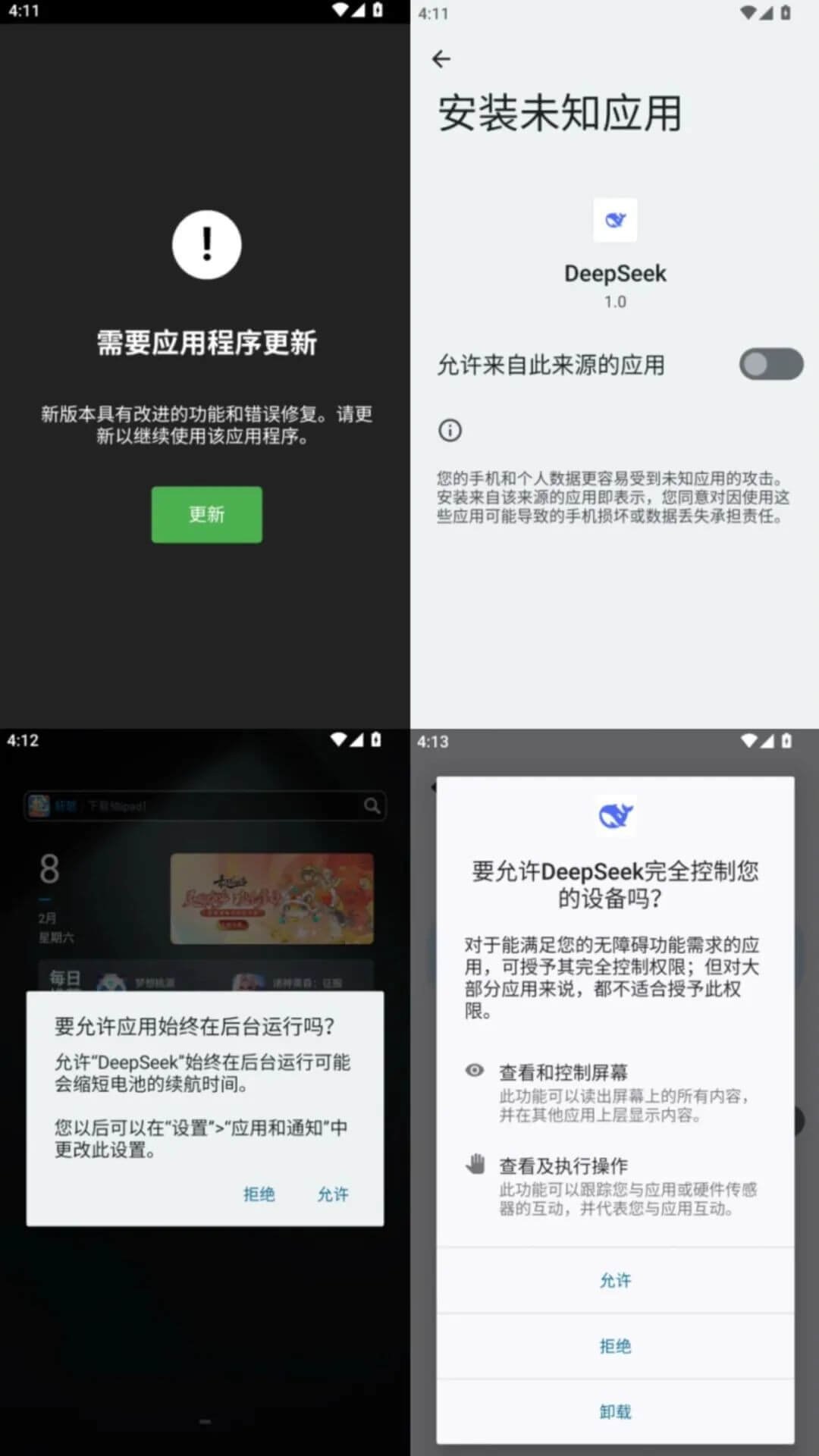
Induce users to “update” (upper left), induce users to install the “poisonous” sub-installation package (upper right), induce users to authorize their background operation (lower left), and induce users to authorize their use of barrier-free functions (lower right).
At the same time, the malicious app also containsIntercept user text messages, steal contacts, and steal mobile application listsAnd other malicious functions that infringe on citizens' personal privacy and information, and malicious behaviors that prevent users from uninstalling. Analyzed,This malicious app is a new variant of the financial theft mobile phone trojan virus。Cybercriminals are likely to use the malicious app for telecommunications network fraud activities, Inducing users to install mobile phone trojan horses that imitate DeepSeek from unofficial channels, thus posing a greater threat to users' personal privacy and economic interests.
In addition to the counterfeit DeepSeek Android client “DeepSeek. In addition to "apk", the National Computer virus Collaborative analysis Platform also found multiple file names:
“DeepSeek. exe”
“DeepSeek. msi”
“DeepSeek. dmg”
Virus sample file,Since DeepSeek has not yet launched an official client program for the Windows platform and macOS platform, the relevant files are counterfeit programs.。 It can be seen that cybercriminals have used counterfeiting DeepSeek as a new way to spread viruses and trojan horses.It is expected that in the coming period of time, the number of viruses and trojan horses that counterfeit various artificial intelligence applications, including DeepSeek, will continue to increase.
National Computer Virus Emergency Response Center
Issue preventive measures
↓↓↓
In response to the trojan virus of this mobile phone, the National Computer Virus Emergency Response Center issued the following preventive measures:
Do not download apps from Web links or QR codes spread by unofficial channels such as text messages, social media software, online disks, etc.,Only download and install the corresponding app through DeepSeek's official website or regular mobile app store。
Keep the pre-installed security protection function of the mobile phone or the third-party mobile phone security software turned on in real time, and keep the mobile phone operating system and security software updated to the latest version.
During mobile phone use,Handle app installation requests initiated by non-users carefully, Once it is found that the App initiates a request for permission to the device manager, background operation, and use of barrier-free functions during the installation process, it should all be rejected.
If you encounter an app program that cannot be uninstalled normally after installation, you should immediately back up important data such as contacts, text messages, photos, chat history, and document files in your mobile phone, and perform safety testing and recovery of your mobile phone under the guidance of after-sales service personnel or professionals of your mobile phone manufacturer. At the same time, pay close attention to whether my social media software and financial software have abnormal login information or abnormal operation information, and whether relatives and friends have received abnormal information sent by my mobile phone number or social media software. In the event of the above-mentioned related situation,,Relevant software vendors and relatives and friends should be contacted in time to explain the relevant situation。
Be vigilant and prevent telecom network fraud tactics against popular app software, Such as “Due to abnormal service on the official website of XXX software, please download the official application through the following link”, “Due to the update of XXX software to the latest version, users need to re-grant background operation and barrier-free function permissions”, etc., to avoid being induced by cybercriminals.
For suspicious files that have been downloaded, you can accessNational Computer Virus Collaborative Analysis PlatformPerform upload detection.


Comment List (0):
Load More Comments Loading. . .